In the intricate web of modern business technologies, securing critical applications is paramount. Application mapping emerges as a vital tool in this context, offering numerous benefits for enhancing application security.
Application mapping, in the context of information technology and cybersecurity, refers to the process of creating a detailed inventory of an organization’s software applications and their interactions. This involves identifying and documenting various components of the applications, such as servers, databases, external services, and APIs, as well as understanding how they communicate and interconnect.
Application mapping is crucial for organizations to comprehend their IT infrastructure’s complexity, manage dependencies, ensure efficient performance, and identify potential security vulnerabilities within their application ecosystem. This comprehensive understanding aids in effective IT management, strategic planning, and bolstering security measures against potential threats.
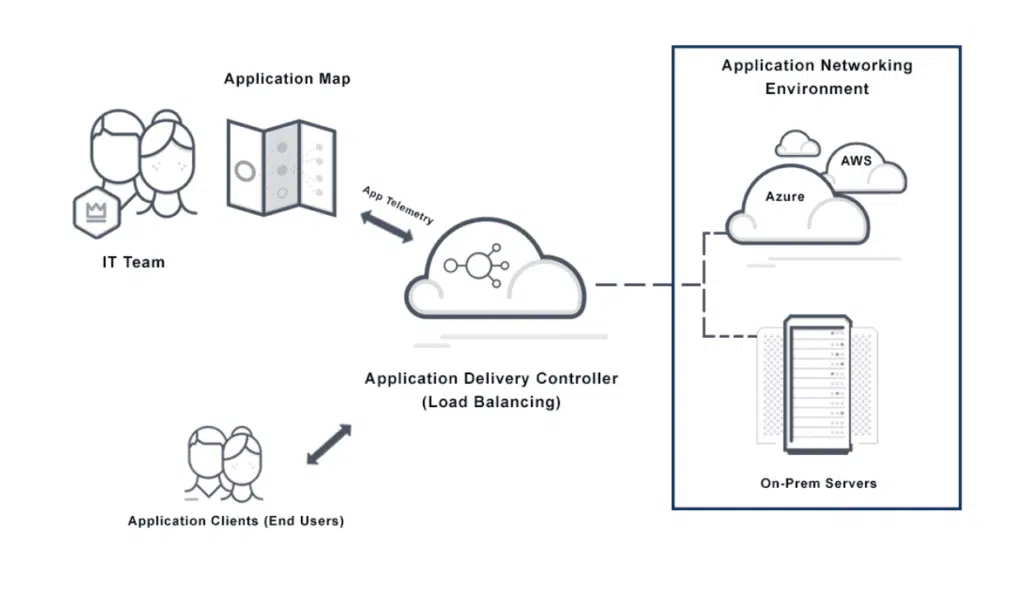
Let’s delve into the five key security advantages that application mapping provides.
1. Enhanced Visibility and Control
Application mapping offers a comprehensive view of an organization’s application landscape. By delineating how applications interact, the data they utilize, and their interdependencies, organizations gain critical insights. This enhanced visibility is not just operationally beneficial but pivotal for security. It enables the identification of potential security vulnerabilities within the application ecosystem, allowing organizations to take proactive steps to address them. Moreover, with greater control over the application environment, organizations can manage their applications more effectively and securely, ensuring a fortified defense against potential threats.
2. Improved Compliance and Risk Management
In today’s regulatory landscape, adherence to industry-specific standards is a major concern for businesses. Non-compliance can lead to significant financial penalties and reputational harm. Application mapping can be a powerful ally in ensuring compliance. By providing a detailed overview of the application landscape, it highlights areas that may not align with current security standards or regulations, such as applications using outdated protocols. This facilitates timely remediation to maintain compliance.
Risk management also benefits from application mapping. Understanding the application ecosystem in its entirety allows for a more accurate assessment of potential risks and the development of targeted mitigation strategies, enhancing the organization’s overall security posture.
3. Efficient Incident Response and Recovery
In the event of a security breach, rapid response is crucial to minimize damage. Application mapping significantly enhances an organization’s ability to respond to and recover from security incidents. With a clear map of the application ecosystem, affected applications and their dependencies can be swiftly identified, isolating the breach and preventing further system infiltration. This knowledge is invaluable in guiding recovery efforts, ensuring applications are restored systematically to reduce downtime and operational impact.
4. Identifying Anomalies and Potential Threats
Early detection of anomalies and threats is critical in preventing security breaches. Application mapping aids in establishing a baseline for normal application behavior and interactions. Deviations from this baseline can signal potential security issues. For example, unexpected communication between an application and an external server might indicate a compromise. A detailed application map is instrumental in detecting such anomalies, enabling quick and effective responses to emerging threats.
5. Data Protection and Privacy Enhancement
In an era where data breaches are rampant and data protection regulations are stringent, safeguarding data privacy is more crucial than ever. Application mapping enhances an organization’s ability to protect data. By tracing data flow within the application ecosystem, organizations gain clarity on data storage, usage, and access. This aids in pinpointing potential data leakage points and implementing necessary security measures. Additionally, understanding data flow is essential for compliance with regulations like the GDPR, helping organizations avoid hefty fines and reputational damage.
Implementing Application Mapping
Here’s a comprehensive guide on how to successfully implement application mapping in an organization:
Setting Clear Objectives and Establishing Scope:
- Defining Goals: Begin by pinpointing what you aim to achieve through application mapping. This could range from enhancing application performance, minimizing downtime, to streamlining IT operations.
- Determining the Scope: Identify the applications to include in your mapping. Will it be limited to critical applications or encompass the entire suite across your organization? This decision hinges on your defined goals and available resources, and it’s crucial for guiding the subsequent steps of the process.
Comprehensive Inventory of Current Applications:
- Cataloging Your Applications: Create an exhaustive inventory of all applications in use. Detail each application’s purpose, user base, and dependencies. This step is pivotal in offering a transparent view of your current application ecosystem, laying the groundwork for identifying areas of improvement and potential integration challenges.
Mapping Inter-Application Dependencies:
- Understanding Interactions: With your inventory at hand, the next phase is to untangle and map out how each application interacts within your network. Leveraging application mapping tools can automate and streamline this process.
- Revealing Complexity: This step uncovers the intricacies of your application network. It helps in comprehending how alterations in one application might ripple through others, aiding in more efficient management and reducing risks associated with changes.
Visual Representation of Your Application Landscape
- Creating a Visual Blueprint: Transform your data into a visual map of your application network. This visualization should capture the network’s structure at various levels, providing insights into its complexity and interconnectivity.
- Insights and Overview: This visual guide is not just a technical asset but a communication tool. It highlights potential bottlenecks and vulnerabilities, flags optimization opportunities, and offers stakeholders an accessible overview of your IT ecosystem.
Conclusion
As the reliance on applications continues to escalate in the business world, recognizing and addressing their security vulnerabilities becomes a non-negotiable aspect of organizational strategy. Application mapping offers an in-depth analysis of the risks inherent in application ecosystems and provides actionable strategies to strengthen their security frameworks. It’s not merely about mitigating risks; it’s about reshaping the security paradigm to align with the evolving digital environment. By prioritizing application mapping, businesses can significantly lower the threat landscape and ensure that their applications are not just operational but also secure and compliant. In a landscape where digital agility is intertwined with security, application mapping is not just a tool – it’s an imperative.



