The world of cybersecurity is a dynamic background, where innovation and threats engage in a constant tug-of-war. With each passing day, new technology empower organizations to bolster their defenses and productivity. Yet, on the flip side, these innovations also present fresh opportunities for malicious actors to breach security and access sensitive data. As 2023 unfolded, it brought a wave of transformation and challenges to the cybersecurity landscape. In this blog post, we’ll dive into the top 5 trends you should keep an eye on for 2024.
Artificial Intelligence (AI)
The rise of Artificial Intelligence (AI) continues to reshape our digital world. AI brings both promise and peril – a double-edged sword in the realm of cybersecurity. Cyber threats are evolving with AI, empowering malicious actors with new tools and capabilities. It is important to note that AI isn’t just for good; it’s also a weapon in the hands of those with ill intentions. The adoption of AI has surged, with over 50% of organizations using it, according to McKinsey & Company.
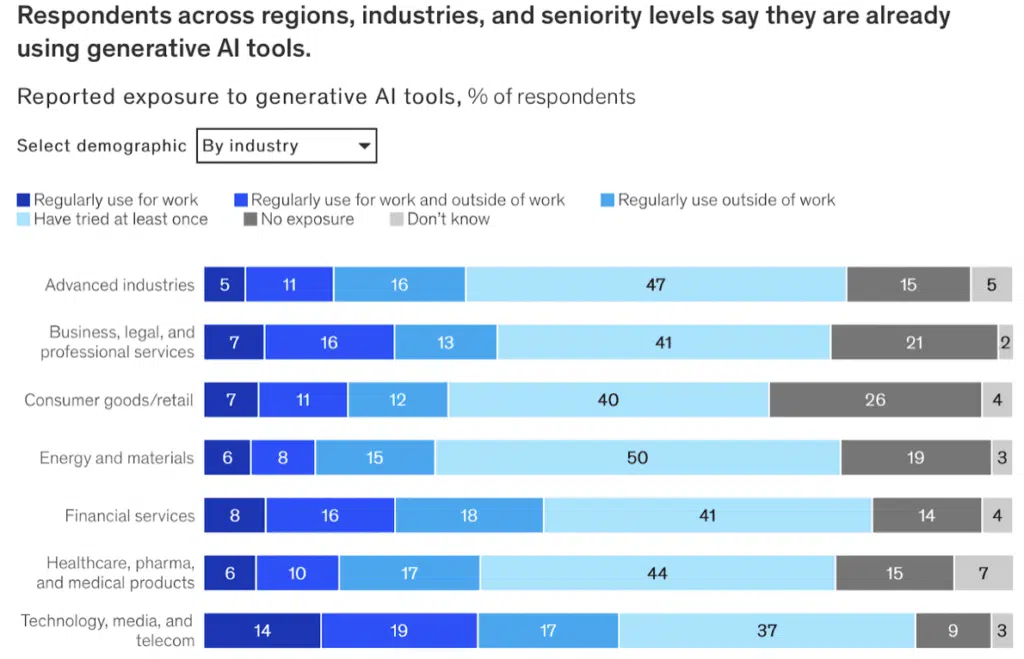
This adoption boosts efficiency and automates routine tasks transforming how businesses operate. For instance, AI is beginning to play a role in code generation, promising faster development. Yet, it can introduce errors, including vulnerabilities in the source code, posing a real threat. To navigate this, we must strike a balance. As of now, AI can enhance productivity, but it can’t replace human expertise. Human oversight and experienced staff are crucial, especially in safeguarding sensitive information and assets.
Passwordless Authentication
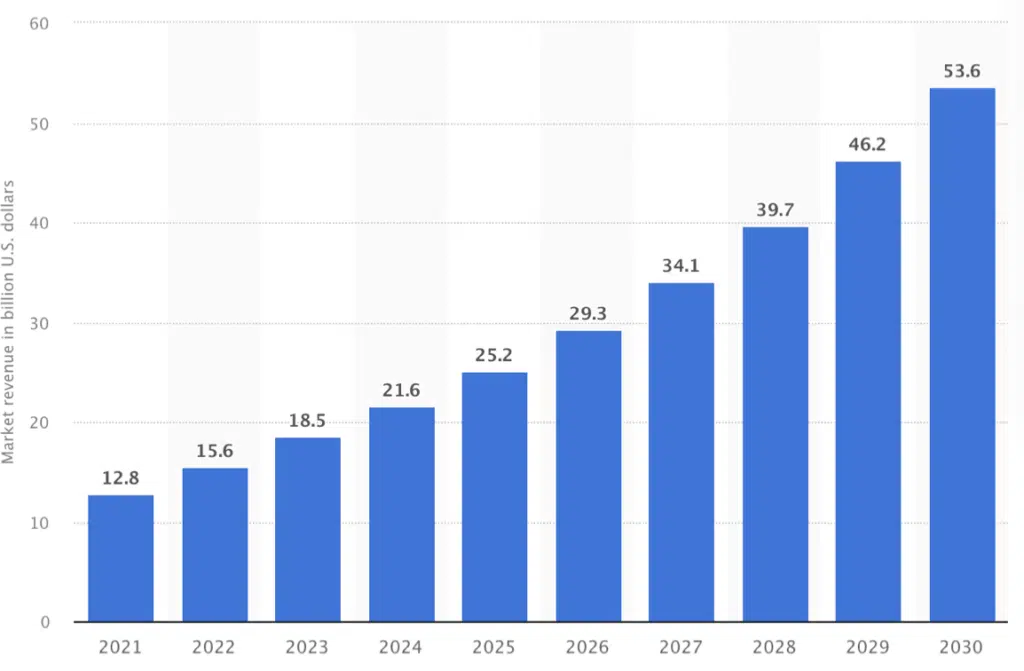
The passwordless authentication market is experiencing substantial growth. In 2022, it was valued at 15.6 billion USD, and projections indicate that it will exceed 53 billion USD by 2030, highlighting a significant upward trajectory.
But what exactly is passwordless authentication? At its core, passwordless authentication is a method that enables users to access applications and IT systems without the need to enter a password or respond to security questions. Its primary goal is to diminish the significance of passwords in the eyes of potential malicious actors. Instead, access is granted through more secure and user-specific means, such as biometric authentication methods like facial recognition or fingerprint scans.
The advantages of passwordless authentication are clear. By relying on biometric factors, it ensures that only individuals who can be accurately authenticated through unique physical or behavioral traits gain access to sensitive data. This approach significantly reduces the susceptibility to various types of attacks, including phishing attempts, credential stuffing, and brute force attacks. This trend is a vital step towards enhancing security and safeguarding sensitive information in organizations across many sectors.
Zero Trust Architecture
The zero trust security model is gaining momentum, and this trend is set to continue in 2024. Zero trust architecture emphasizes continuous authentication and validation for all users, both inside and outside an organization’s network, to access applications and data. This approach enhances security by ensuring that user access is consistently verified.
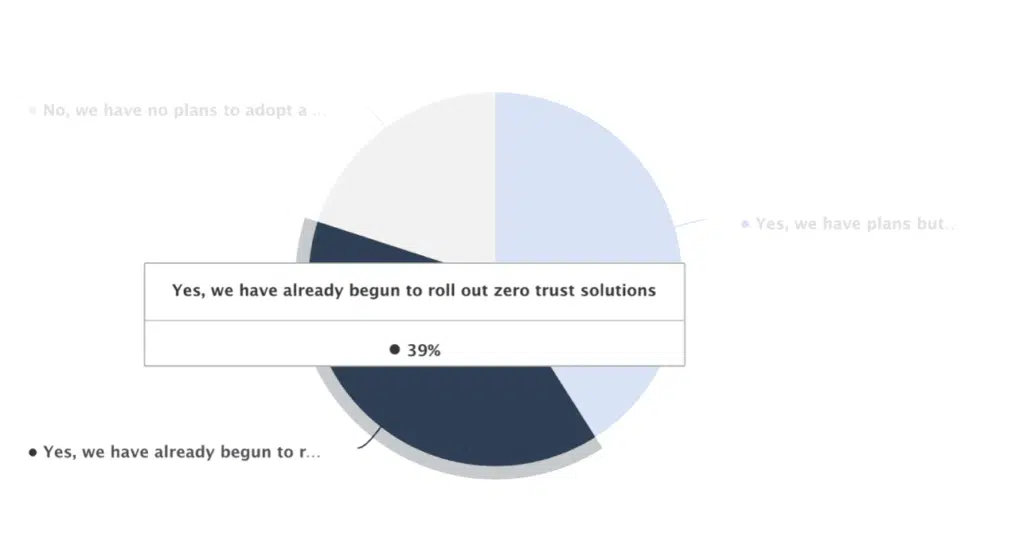
In a 2022 global survey, 39% of respondents had already begun implementing zero trust solutions.
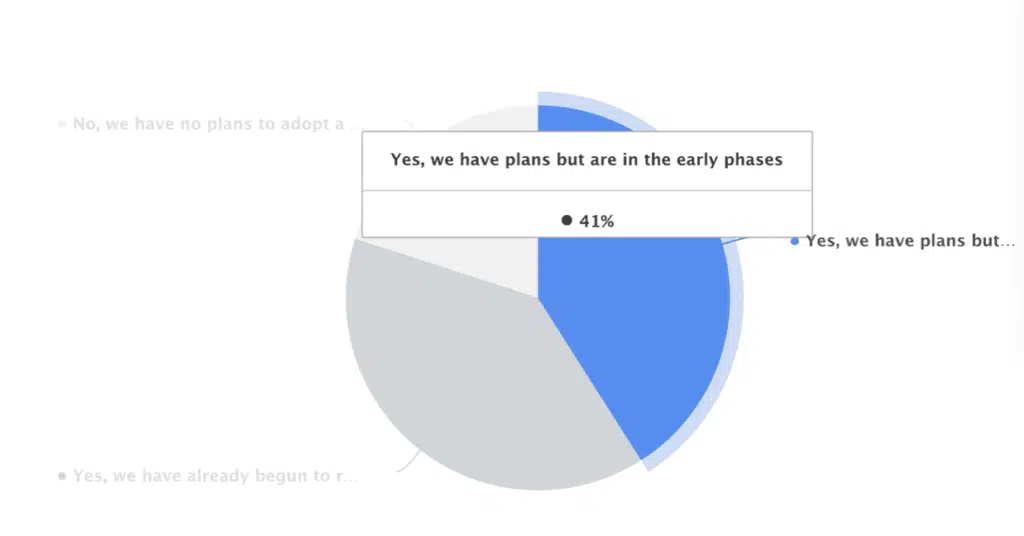
Additionally, 41% of respondents worldwide reported plans to adopt a zero trust strategy, with early-phase initiatives underway.
Despite these promising numbers, Gartner notes that only 1% of large organizations have fully implemented a mature zero trust program. However, the forecast indicates that by 2026, 10% of large organizations will have mature programs in place. This growth projection underscores the industry’s shift towards embracing zero trust security.
With the majority of companies expressing interest in this model, 2024 presents an opportune time to explore its advantages and assess its suitability for your organization.
Cybersecurity Skills Gap
The evolving threat landscape and the constant innovation of malicious actors has increased the demand for cybersecurity professionals. Unfortunately, the current supply of such professionals falls short, posing a significant challenge for organizations seeking the expertise they require. The reality is that, with a developer to application security professional ratio of 500:1, many companies face a critical skills gap.
To address this pressing issue, organizations should consider several proactive measures. First, they can invest in training their existing staff to develop in-house expertise. Empowering developers to take on security responsibilities is a valuable step in bridging the skills gap. Additionally, establishing a security champions program within the organization can help identify and nurture individuals with a keen interest and aptitude for cybersecurity.
Lastly, exploring partnerships with cybersecurity vendors can provide access to external expertise and resources. In today’s interconnected world, security is not a luxury but a necessity. Organizations must be proactive in closing these skills gaps through a combination of training, internal empowerment, and strategic collaboration.
Threat Detection, Investigation and Response (TDIR)
Threat detection, investigation, and response (TDIR) is a crucial strategy for mitigating cybersecurity threats and enhancing threat detection efficiency. In today’s dynamic digital landscape, the attack surface for organizations is continually expanding, and this trend is expected to persist in the coming years. It’s imperative for organizations to gain a comprehensive understanding of their risks and implement robust monitoring tools to proactively safeguard against potential cyberattacks.
Levi Consulting predicts that by 2026, over 60% of TDIR capabilities will rely on management data to validate and prioritize identified threats, a significant increase from the current 5%. This emphasizes the growing importance of data-driven approaches in threat management. Fortunately, new solutions are emerging in the market to assist organizations in identifying threats, detecting attacks, and responding to incidents effectively. Organizations should consider leveraging these innovative tools to bolster their cybersecurity defenses.
One such tool is Bright’s Dev-Centric Dynamic Application Security Testing (DAST) solution. Our solution has played a pivotal role in helping numerous organizations identify vulnerabilities early in the Software Development Life Cycle (SDLC). By addressing vulnerabilities at an early stage, organizations not only bolster their security but also save both time and resources in the long run.
If you’re ready to take the first step in fortifying your organization’s cybersecurity posture, schedule a meeting with our sales team today. Our experts are keen to provide you with further insights and guidance on how our solution can assist in safeguarding your organization from potential threats.




