The information age has advanced the way in which our society generates, stores and exchanges information. Hyperconnectivity, availability and business networking are great benefits of this era. However, we are facing significant new challenges in the realm of cybersecurity and information security, dictating the need for new solutions and a fresh approach to keep up with ever-evolving threats.
Information security is one of the most important fields in the information technology sector with data and application security taking front and center as the most important areas of focus.
As the pioneer in AIAST® (Artificial Intelligence Application Security Testing) solutions, Bright combines the best of all the approaches currently used in the realm of application security. We provide innovative solutions that have never been seen before. Bright delivers various AIAST® tools powered by genetic algorithms and reinforcement learning engine.
Bright’s solutions take an active approach to application security testing and are powered by an adaptive engine that enables the discovery of different sets of issues and vulnerabilities, including business logic issues which until now were considered impossible to detect by an automated solution.
Bright’s AIAST® is a SaaS solution that combines Application Security Testing with AI. The technology is powered by a proprietary deep learning algorithm that creates its own sophisticated malicious scenarios covering both known vulnerabilities and new, previously discovered vulnerabilities.
The OWASP Top 10 list details the 10 most prevalent and high priority risks that most applications face and includes:
- Injection
- Broken Authentication
- Sensitive Data Exposure
- XML External Entities (XXE)
- Broken Access Control
- Security Misconfigurations
- Cross-site Scripting (XSS)
- Insecure Deserialization
- Using Components with known vulnerabilities
- Insufficient logging and monitoring
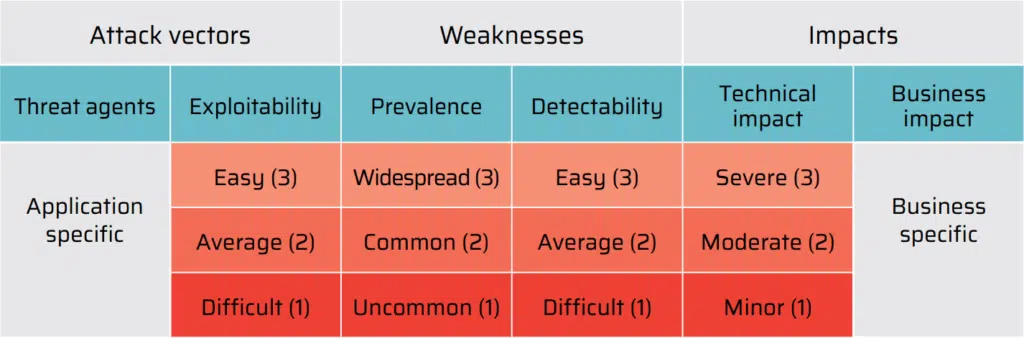
The OWASP Risk Rating Methodology describes the likelihood and the impact of security risks outlined in the OWASP Top 10 list. As for the threat model, a threat agent uses an attack vector to exploit a security weakness that is exposed to an asset or a function due to the lack of security controls.
The OWASP Risk Rating Methodology describes the likelihood and the impact of security risks outlined in the OWASP Top 10 list. As for the threat model, a threat agent uses an attack vector to exploit a security weakness that is exposed to an asset or a function due to the lack of security controls.
The risk level is calculated based on a table that determines the level of impact that a threat agent can introduce with each of the Top 10 vulnerabilities. The table provides a rating on a scale of 1 to 3 for each of the risk factors. Threat agents and business impacts are described as they are specific to every application and its business objectives. Below is a table outlining the risk levels: