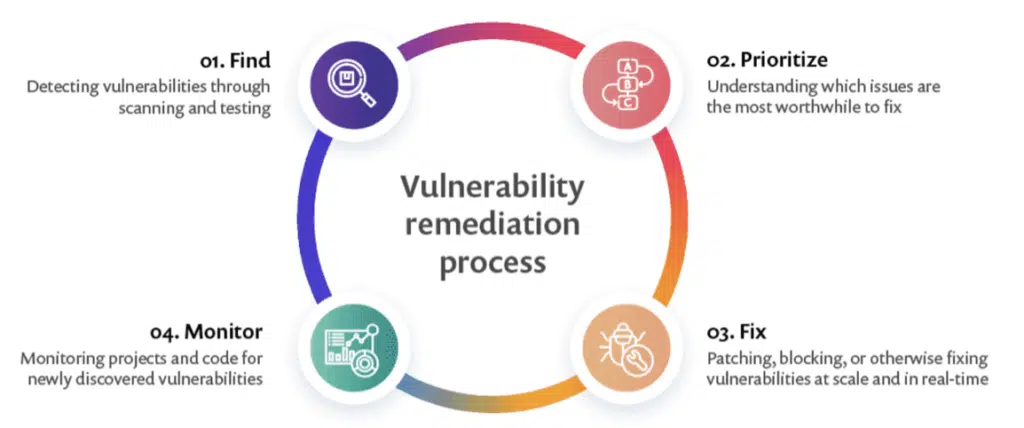
Modern day organizations face a constant barrage of cyber threats, making it imperative to implement robust vulnerability management processes. Vulnerability management is a systematic approach to identifying, evaluating, treating, and reporting on security vulnerabilities in systems and their associated software. In this blog post, we’ll delve into the four crucial steps of vulnerability management process and explore the significance of continuous vulnerability assessments.
Step 1: Perform Vulnerability Scan
The foundation of vulnerability management lies in performing thorough vulnerability scans. A vulnerability scan is a systematic and automated process designed to identify potential weaknesses or vulnerabilities within a computer system, network, or application. The primary objective of a vulnerability scan is to assess the security posture of an organization’s digital assets by discovering and highlighting areas that may be susceptible to exploitation by malicious actors. This process consists of four essential stages:
Network Scanning
Conducting a scan involves pinging or sending TCP/UDP packets to network-accessible systems to identify their presence. This initial step is crucial for creating a comprehensive inventory of the systems within an organization’s network. By actively probing these systems, security teams can pinpoint potential weak points, ensuring a thorough examination of the attack surface. Network scanning serves as the reconnaissance phase, helping organizations understand the scope of their digital infrastructure and identify potential areas that require security reinforcement.
Port and Service Identification
Once systems are identified, the next step is to determine open ports and services running on these systems. This granular understanding is essential for cybersecurity teams as it provides insights into the specific pathways that malicious actors could exploit. Identifying open ports and services enables organizations to tailor their security measures to protect these entry points, enhancing overall defense against cyber threats.
Detailed System Information
For a comprehensive assessment, remote logins to systems are initiated to gather detailed information about the system’s configuration and potential vulnerabilities. This step goes beyond surface-level scans, allowing security professionals to delve into the intricacies of each system. By collecting detailed system information, organizations can better understand the unique risks associated with each system and tailor their response to address specific vulnerabilities effectively.
Correlation with Known Vulnerabilities
The gathered system information is then correlated with known vulnerabilities, helping prioritize and address potential threats effectively. This correlation step is pivotal in the vulnerability management process, as it allows organizations to match identified vulnerabilities with existing knowledge about their severity and potential exploits. By aligning current vulnerabilities with known risks, security teams can allocate resources more efficiently, focusing on addressing the most critical issues first and reducing the overall risk profile.
Step 2: Assess Vulnerability Risk
After performing the vulnerability scan, a thorough risk assessment is needed. Risk assessments are integral to effective risk management and provide organizations with insights to make informed decisions about resource allocation, security measures, and overall business strategy. When assessing risk, consider the following factors:
True or False Positive
Determine whether the identified vulnerability is genuine or a false positive. This step is crucial in avoiding unnecessary panic or resource allocation for non-existent threats. Security teams need to validate the accuracy of the identified vulnerabilities to ensure their efforts are focused on real risks.
Remote Exploitation
Evaluate the likelihood of someone exploiting the vulnerability directly from the internet. Understanding the remote exploitation potential helps organizations gauge the urgency of addressing specific vulnerabilities, especially in the context of evolving cyber threats and the increasing sophistication of attackers.
Exploit Difficulty
Assess how challenging it would be to exploit the vulnerability. This factor helps prioritize vulnerabilities based on the skill level required for exploitation. High difficulty may reduce the immediate risk, while low difficulty indicates a more pressing need for mitigation.
Existence of Exploit Code
Check if there is known and published exploit code for the identified vulnerability. The presence of exploit code in the public domain increases the urgency of addressing the vulnerability, as it suggests that attackers may already have the tools to exploit the weakness.
Business Impact
Understand the potential impact on the business if the vulnerability is exploited. This involves assessing the consequences in terms of data loss, service disruption, financial loss, and damage to reputation. The business impact analysis guides organizations in making informed decisions on prioritizing vulnerabilities based on their potential harm.
Security Controls
Consider existing security controls that may reduce the likelihood or impact of exploitation. Evaluating the effectiveness of current security measures helps organizations understand their overall resilience and guides decisions on whether additional controls or enhancements are necessary.
Vulnerability Age
Determine how long the vulnerability has existed on the network. The age of a vulnerability provides insights into the organization’s historical security posture and helps prioritize older vulnerabilities that may have been overlooked in previous assessments.
Step 3: Prioritize and Address Vulnerabilities
Once vulnerabilities are assessed, they need to be prioritized based on the identified risks. Treatment options include:
Remediation
Fully fixing or patching a vulnerability to prevent exploitation. Remediation is a proactive and comprehensive approach, aiming to eliminate the vulnerability entirely by applying patches, updates, or configuration changes. It represents a decisive action to enhance security by addressing the root cause of the vulnerability, reducing the risk of exploitation.
Mitigation
Lessening the likelihood and/or impact of a vulnerability being exploited, providing time for eventual remediation. Mitigation involves implementing interim measures to reduce the risk associated with a vulnerability while plans for full remediation are underway. This strategic approach recognizes the urgency of addressing immediate threats and offers a temporary shield, allowing organizations to buy time for thorough and permanent fixes.
Acceptance
Taking no action when a vulnerability is deemed low-risk, and the cost of fixing outweighs the potential impact. This decision is typically based on a careful assessment of the risk’s low impact or the understanding that existing compensatory controls sufficiently minimize the threat.
Step 4: Continuous Vulnerability Management
Vulnerability management is an ongoing process that requires regular assessments. Continuous vulnerability management allows organizations to:
Track Progress
Understand the speed and efficiency of the vulnerability management program over time. Tracking progress is essential for organizations to measure the effectiveness of their vulnerability management efforts. By analyzing the trends and improvements in identifying and addressing vulnerabilities, they can fine-tune their strategies for better outcomes and increased resilience against potential threats.
Adapt to Changes
Adjust strategies based on evolving threats and changes in the organizational landscape. The dynamic nature of the cybersecurity landscape demands adaptability. By staying informed about the latest threat intelligence and adjusting their approach in real-time, organizations can enhance their ability to withstand evolving cyber risks.
Enhance Security Posture
Strengthen the overall security posture by addressing emerging vulnerabilities promptly. Continuous vulnerability management goes beyond mere identification; it involves swift action to address newly discovered vulnerabilities.
Conclusion
In conclusion, vulnerability management is a critical component of an effective cybersecurity strategy. By following the four key steps and embracing continuous vulnerability assessments, organizations can stay ahead of potential threats, minimize their attack surface, and foster a resilient security environment. Prioritizing and addressing vulnerabilities proactively is not just a best practice; it’s a necessity in the world of cybersecurity.



