What Are Vulnerability Assessment Tools?
Vulnerability assessment tools are specialized software designed to identify, classify, and prioritize vulnerabilities in computer systems, applications, and network infrastructures. They provide a detailed analysis of the potential points of exploit on a system to help identify the necessary actions to mitigate the risk. By providing insights into the vulnerabilities that a system may have, these tools enable organizations to put the necessary security measures in place.
These tools conduct an exhaustive examination of the system for any potential security risks. They scan the network for outdated software, missing patches, incorrect configurations, and any other potential risk areas that could be exploited by hackers. The results of these scans are then used to formulate a comprehensive report of the system’s vulnerabilities, which can then be used by IT professionals to address and resolve the identified issues.
It’s important to remember that vulnerability assessment tools are not a one-time solution. Cyber threats evolve continuously, and new vulnerabilities can emerge at any time. Therefore, regular assessments are crucial to maintaining an up-to-date security posture.
In this article:
- Types of Vulnerability Assessment Tools
- Key Features of Vulnerability Assessment Tools
- Notable Vulnerability Assessment Tools
Types of Vulnerability Assessment Tools
Application Vulnerability Assessment Tools
Application vulnerability assessment tools focus on identifying vulnerabilities within an organization’s software applications. These tools carry out static and dynamic analysis of the applications to identify potential security weaknesses.
These tools are particularly effective at identifying vulnerabilities such as SQL injection, cross-site scripting, buffer overflows, and other common application-level vulnerabilities. They provide detailed reports on the identified vulnerabilities, along with recommendations for remediation.
Network Vulnerability Assessment Tools
Network vulnerability assessment tools are designed to scan an organization’s network for any vulnerability that could be exploited. They perform an in-depth analysis of the network infrastructure, checking for weak points in servers, hosts, devices, and other network components.
These tools are capable of identifying a wide range of vulnerabilities, including outdated firmware, weak passwords, misconfigured systems, and known exploits. Once these vulnerabilities are identified, the tool provides detailed reports and recommendations on how to remediate them.
Database Vulnerability Assessment Tools
Database vulnerability assessment tools focus specifically on identifying vulnerabilities in an organization’s databases. These tools scan the database management systems for any potential security weaknesses, misconfigurations, or other vulnerabilities that could be exploited.
These tools are vital for organizations that store sensitive data in their databases. They help identify weak points in the database security, providing detailed reports on the identified vulnerabilities, and recommendations for remediation.
Endpoint Vulnerability Assessment Tools
Endpoint vulnerability assessment tools focus on identifying vulnerabilities at the endpoints of an organization’s network. Endpoints can include laptops, desktops, mobile devices, and other devices that connect to the network.
These tools are essential for organizations with a large number of devices connecting to their network. They help identify vulnerabilities such as missing patches, outdated software, and other potential security weaknesses at the endpoints. They provide detailed reports on the identified vulnerabilities, along with recommendations for remediation.
Key Features of Vulnerability Assessment Tools
Scanning
One of the most essential features of vulnerability assessment tools is their ability to scan your systems. These tools run automated scans across your network, analyzing every device, application, and system for potential vulnerabilities.
Scanning is not a one-time activity but a continuous process. As new vulnerabilities are discovered every day, it is crucial to regularly scan your systems to stay apprised of any new potential threats. Some advanced vulnerability assessment tools even offer real-time scanning, providing continuous visibility into your security posture.
Learn more in our detailed guide to vulnerability scanner (coming soon)
Vulnerability Detection
After scanning your systems, vulnerability assessment tools unearth any potential vulnerabilities. They can detect a wide range of vulnerabilities from misconfigurations and unpatched software to insecure network protocols and beyond.
Vulnerability detection is usually based on databases of known vulnerabilities such as the Common Vulnerabilities and Exposures (CVE) database. The tools match the scan results with the vulnerabilities in these databases to identify any potential threats.
Moreover, some advanced tools also incorporate artificial intelligence and machine learning to predict and identify unknown vulnerabilities. This can be particularly useful in mitigating zero-day exploits—vulnerabilities that are unknown to the vendor and for which no patch exists.
Threat Assessment
Once vulnerabilities are detected, vulnerability assessment tools evaluate the potential impact of these vulnerabilities. This is where threat assessment comes into play.
Threat assessment is a process of determining the potential damage a vulnerability could cause if exploited. It takes into consideration various factors such as the severity of the vulnerability, the value of the data or system at risk, and the likelihood of the vulnerability being exploited.
Using this information, the tools can prioritize the vulnerabilities, helping you to address the most critical ones first. This way, you can manage your resources effectively and minimize the potential impact of a security breach.
Reporting and Visualization
After scanning, detecting, and assessing threats, vulnerability assessment tools provide detailed reports of their findings. These reports typically include a list of identified vulnerabilities, their severity, and recommended remediation actions.
Some tools also offer visualization features, presenting the data in easy-to-understand formats like charts, graphs, and heat maps. This can be particularly useful in understanding the overall security health of your systems and in communicating the findings to non-technical stakeholders.
Moreover, the reporting feature can also help in compliance reporting. By demonstrating your organization’s proactive approach to identifying and mitigating vulnerabilities, you can meet the requirements of various regulatory standards like GDPR, HIPAA, and PCI DSS.
Learn more in our detailed guide to vulnerability assessment report (coming soon)
Integration with Other Tools
To maximize their effectiveness, vulnerability assessment tools often integrate with other security tools. For instance, they can integrate with Intrusion Detection Systems (IDS), Security Information and Event Management (SIEM) systems, and patch management tools.
These integrations allow for a more holistic approach to security. For instance, once a vulnerability is detected, the information can be directly fed into a patch management tool for mitigation. Similarly, by integrating with an IDS, the tools can correlate vulnerability data with intrusion attempts, providing more context to potential threats.
Notable Vulnerability Assessment Tools
1. Bright Security

Bright Security is a powerful dynamic application security testing (DAST) tool that offers a comprehensive, intuitive, and user-friendly platform to manage and mitigate cyber threats. It is equipped with advanced features like real-time threat intelligence, automated vulnerability scanning, and detailed reporting. With Bright Security, you can gain a holistic view of your security posture and make informed decisions about your cybersecurity strategy.
Bright Security’s key strength lies in its ability to identify complex vulnerabilities with zero false positives. Its real-time threat intelligence feature keeps you updated about the latest threats, allowing you to stay one step ahead of cybercriminals. Moreover, its detailed reports facilitate easy comprehension and tracking of vulnerabilities, enabling you to prioritize your efforts effectively.
Get a free Bright Security account and start testing application vulnerabilities!
2. Nessus

Nessus is a popular network vulnerability assessment tool. It provides features designed to help you identify, assess, and rectify security vulnerabilities. Nessus offers tools for vulnerability scanning, configuration auditing, asset profiling, and more. It is known for its speed, accuracy, and thoroughness in scanning networks.
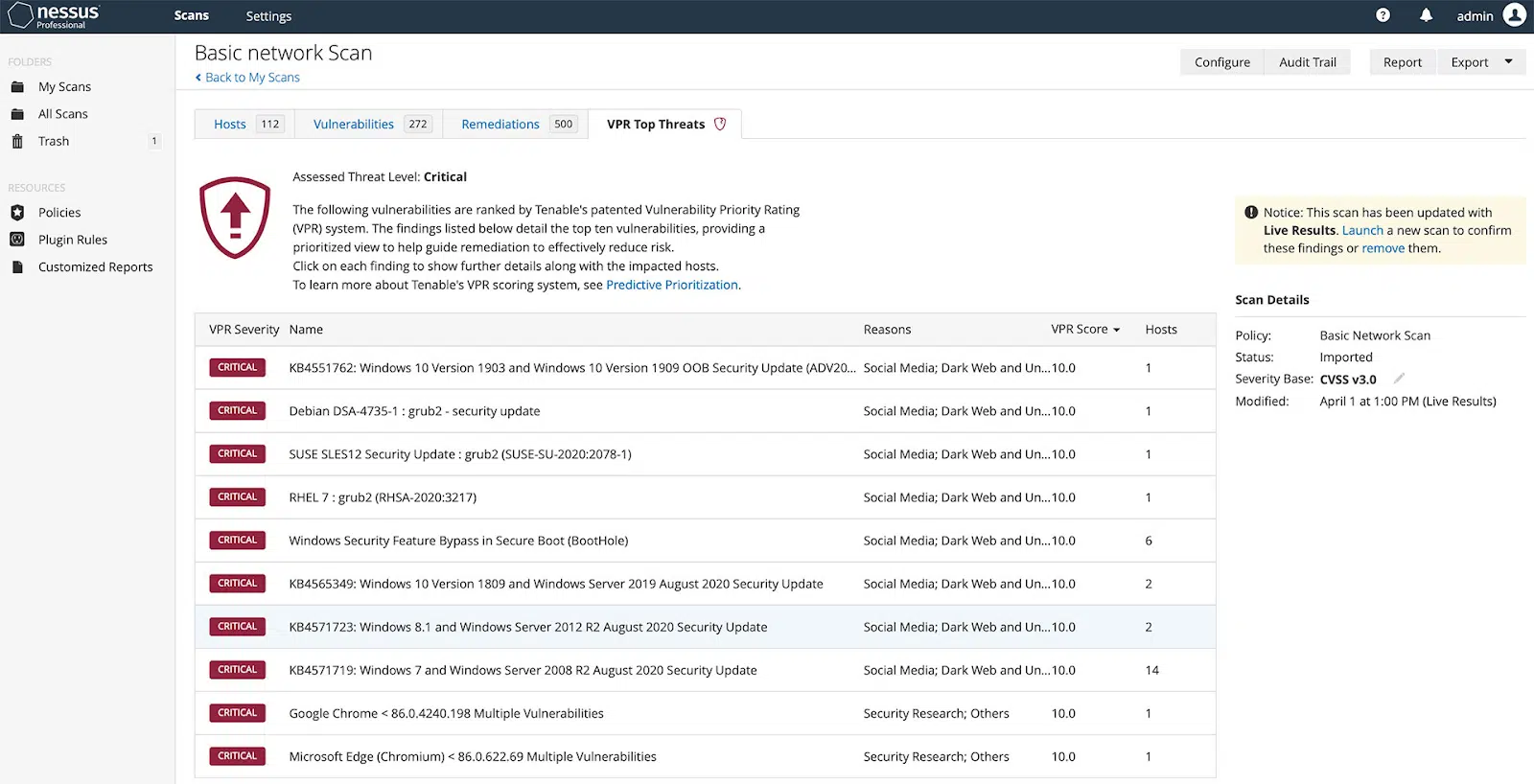
Source: Nessus
Nessus’s provides a comprehensive vulnerability database, frequent updates, and easy-to-use interface. Its ability to scan a wide range of devices, including network devices, databases, and web servers, makes it a versatile tool suitable for organizations of all sizes. Moreover, its extensive reporting capabilities enable you to understand your vulnerabilities in-depth and plan your mitigation strategies accordingly.
3. Qualys

Qualys is a cloud-based network vulnerability assessment tool. Its primary function is to identify vulnerabilities in your network and provide recommendations for their remediation. Qualys offers speed, scalability, and accuracy in its vulnerability scans.
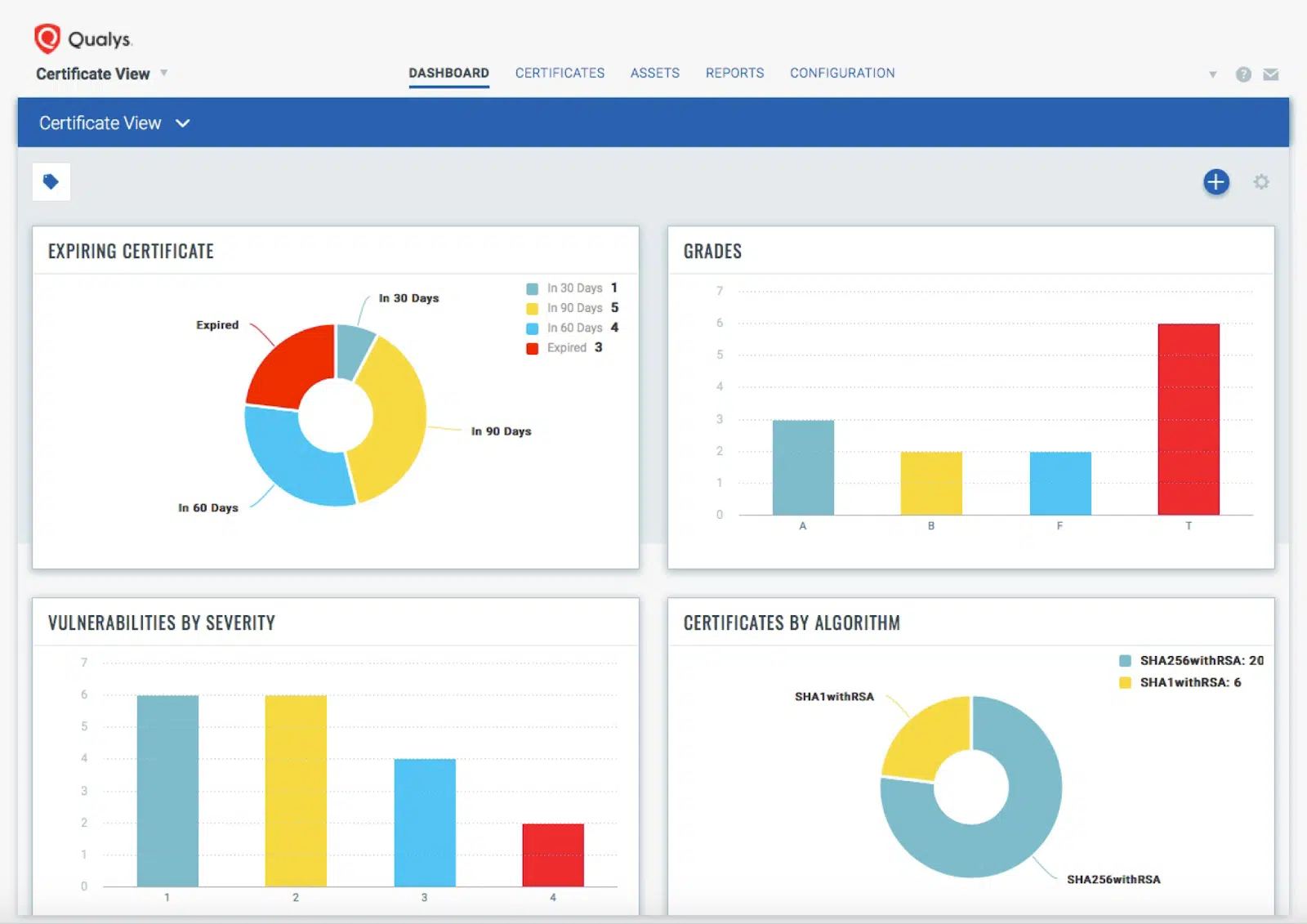
Source: Qualys
Qualys’s cloud-based nature allows it to perform scans without the need for any hardware or software installations. This scalability makes it suitable for both small businesses and large enterprises. Furthermore, its real-time threat updates ensure that you are always aware of the latest vulnerabilities.
4. OpenVAS

OpenVAS is a free and open-source application vulnerability assessment tool. It offers a suite of tools for vulnerability scanning, management, and reporting.
Source: Wikimedia
OpenVAS’s strength lies in its vibrant community of users and developers, who continually work on improving the tool and keeping it updated with the latest threat intelligence. Its range of plugins allows for customization according to your specific needs. Additionally, its detailed reporting capabilities help you understand your vulnerabilities and devise effective mitigation strategies.
5. Nexpose

Nexpose, developed by Rapid7, is a network vulnerability management tool that offers real-time insights into your security posture. It is known for its dynamic risk scoring, which evaluates vulnerabilities in the context of their potential impact on your business.
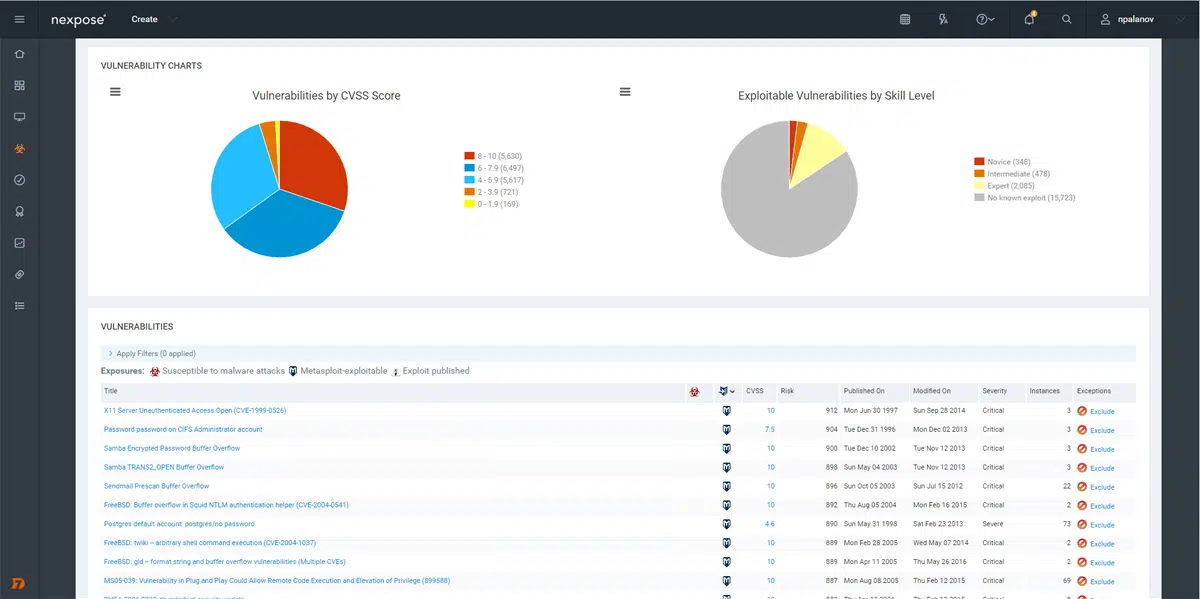
Source: Rapid7
Dynamic risk scoring helps you prioritize your efforts based on the potential damage a vulnerability could cause. This context-based approach allows for more effective vulnerability management. Moreover, its integration capabilities with other security tools further enhance its effectiveness as a comprehensive security solution.
Conclusion
In conclusion, vulnerability assessment tools are indispensable in the cybersecurity arsenal of any organization. These tools scan, detect, and assess potential vulnerabilities in a system’s network, applications, databases, and endpoints. They offer vital capabilities such as automated scanning, threat assessment, detailed reporting, and integration with other security tools.
Implementing and regularly using vulnerability testing tools can significantly bolster an organization’s cybersecurity posture, enabling them to identify and address vulnerabilities proactively, ultimately helping them stay ahead of evolving cyber threats. As cybersecurity continues to be a paramount concern for any organization, the importance and relevance of vulnerability assessment tools continues to grow.



