This blog post announces the August 2021 Update for Bright.
We added some new features and product enhancements that will make your experience even better.
New Features:
New engine logs download
From now on there is no need to worry about downloading large engine logs. When needed, the full engine logs will be generated offline and will be available for download via an email notification.
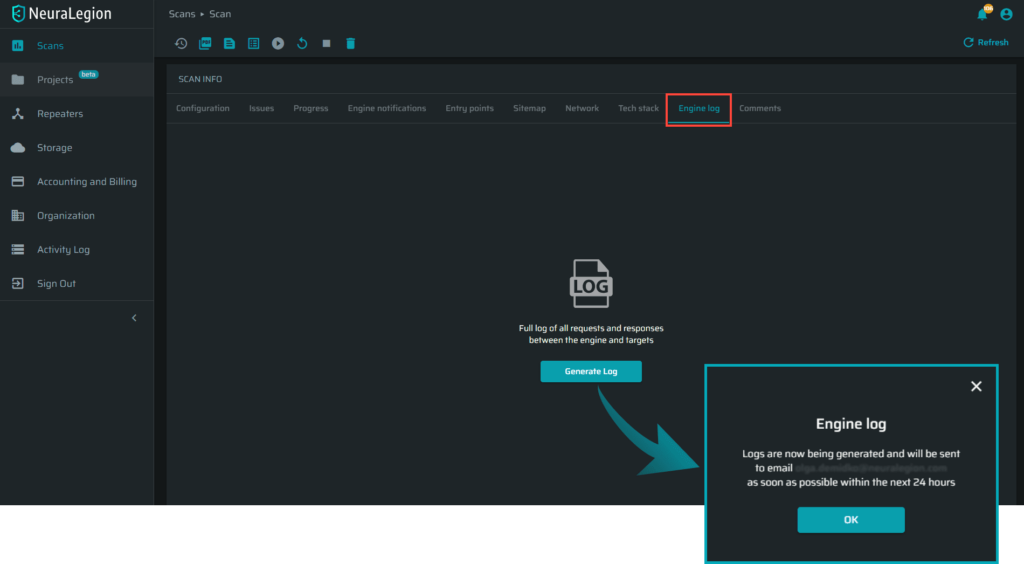
Check it out!
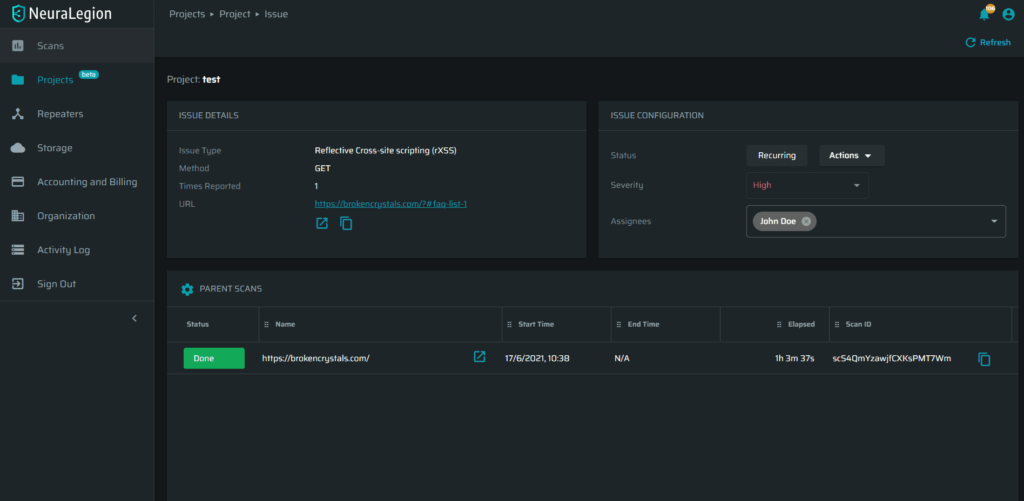
New project issues page
Check out the new ‘Project Issue’ page, where each finding can be tracked over time over multiple scans.
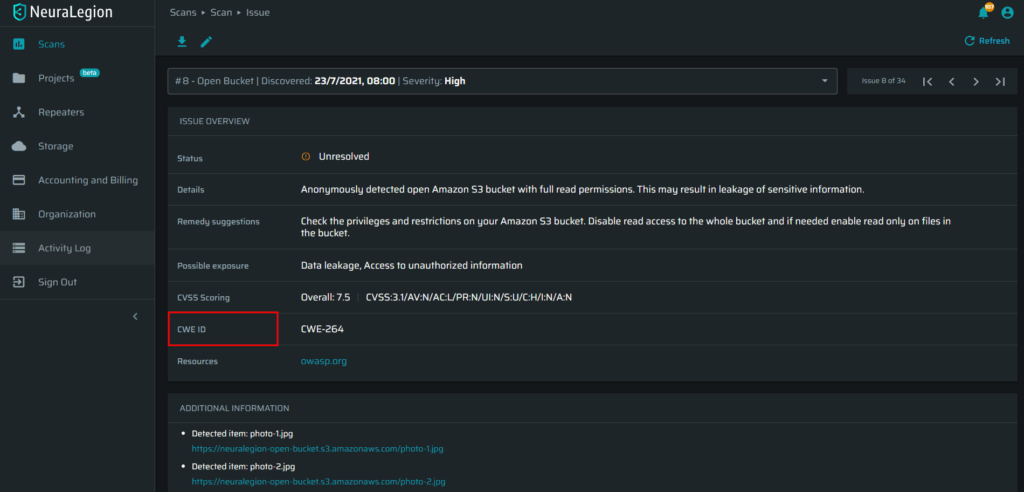
Added CWE ID to found issues
We added the CWE ID for found issues to further help security teams triage the scan results more effectively
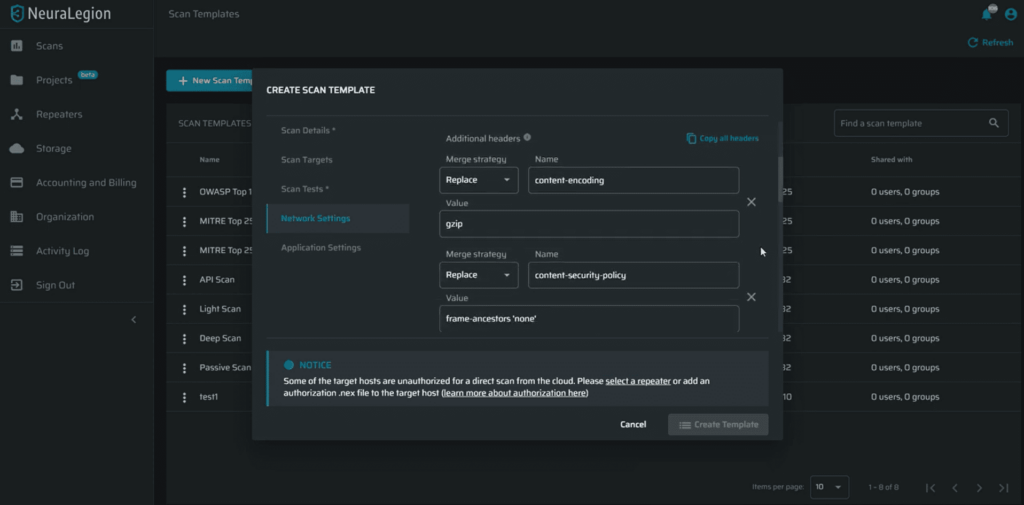
New ‘Smart Copy-Paste’ for headers input
Tired of manually filling out the required ‘Headers’ one-by-one?
Check out our new ‘smart copy’ option with the new ‘Headers’ field!
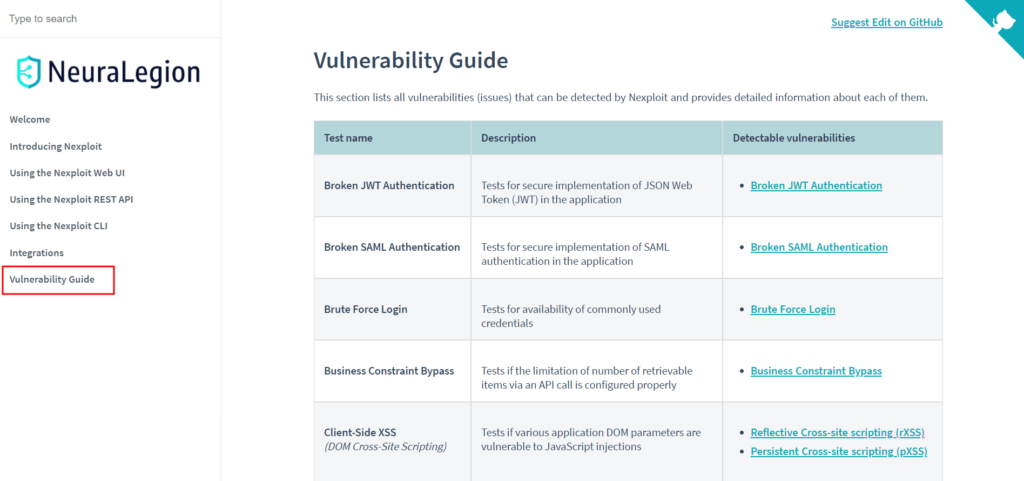
New ‘Vulnerability Guide’ section on the Knowledge Base
We released a new section on our knowledge base with detailed information about the tests we do, and how to remediate them!
Improvements:
Crawler improvements
Significant improvements to crawler speed and stability.

Authentication Object Improvements
Improvements to the ‘Browser Based Form Authentication’ object

UX/UI improvements
Check out our new ‘Scan Summary’ page, field inputs and other UX improvements to make your experience even better!