What is Application Security Testing?
Application security testing (AST) is an umbrella term for methodologies that assist in finding and eliminating software vulnerabilities. The security testing process includes tests, analysis, and reports that provide insight into the security level of a software program.
You can apply the AST process across various phases of the software development lifecycle (SDLC). AST can help catch and remediate software vulnerabilities before deployment to production, reducing the scope of vulnerabilities persisting after deployment. You can also apply AST in production to enable continuous detection of critical threats.
This is part of an extensive series of guides about cybersecurity.
In this article:
- 5 Application Security Testing (AST) Solutions
- 3 Types of Application Security Testing
- Application Security Testing Best Practices
5 Application Security Testing (AST) Solutions
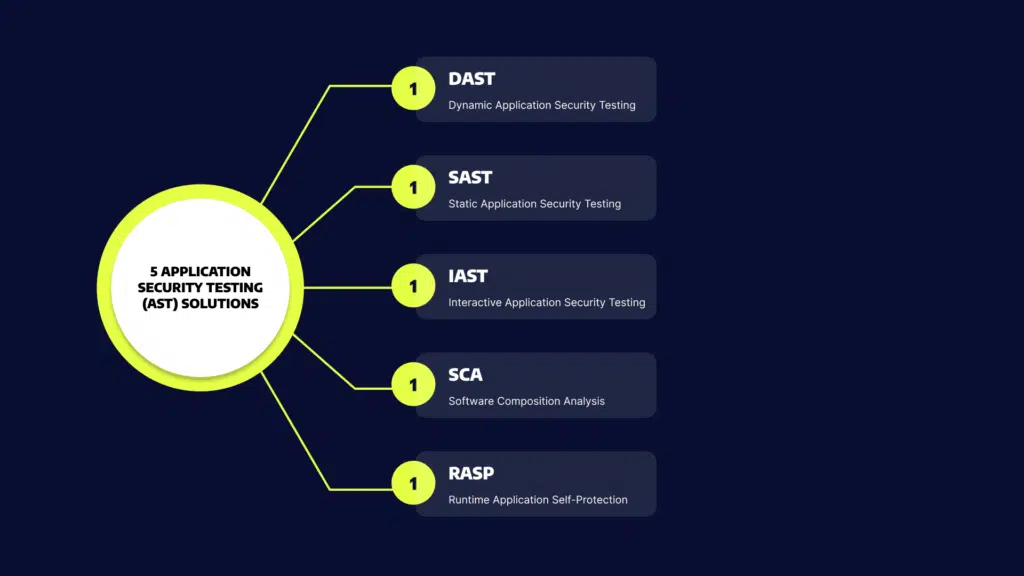
AST won’t happen without tools. Let’s review five types of solutions that can help you test software through the SDLC – from development to production.
Static Application Security Testing (SAST)
SAST is a form of white-box testing that involves analyzing at-rest source code. SAST tools look for vulnerabilities in the source code that external parties can exploit.
You can use SAST to the source code of your applications, bytes, and binaries. After analyzing your code, the tool flags exploitable design and coding flaws.
Most SAST scans use a collection of predefined rules to specify coding errors to address. You can also use a SAST scan to detect common security vulnerabilities, such as input validation errors, stack buffer overflow, and SQL injection.
You can implement SAST during development and quality assurance (QA) and integrate the tool with your integrated development environments (IDEs) and continuous integration (CI) servers.
Related content: Read our guide to SAST
Dynamic Application Security Testing (DAST)
DAST is a form of black-box testing that simulates external attacks on a running application. DAST aims to find architectural weaknesses and security vulnerabilities.
DAST solutions attempt to penetrate the application from the outside, often by looking for vulnerabilities and flaws in exposed interfaces.
SAST tools perform a line-by-line scan of your application’s source code while it is at rest, while DAST is executed when the application is running. DAST can be used to test an application running in a development or testing environment, or while it is running in production.
Related content: Read our guide to DAST
Interactive Application Security Testing (IAST)
IAST tools and testers scan the post-build source code of your application in a dynamic environment. The test is usually executed in a test or QA environment and in real-time while the application is running. You can employ IAST to identify problematic lines of code and get alerts that prompt immediate remediation.
IAST looks directly at the source code post-build in a dynamic environment through the instrumentation of the code. It involves deploying agents and sensors into the application and analyzing the code to detect vulnerabilities. You can easily integrate IAST into your continuous integration / continuous delivery (CI/CD).
Software Composition Analysis (SCA)
SCA tools automatically scan the codebase of your application to provide visibility into open source software usage. SCA tools can identify all open source components in your codebase, the license compliance data of the components, and detect common security vulnerabilities. Some SCA tools can also prioritize open source vulnerabilities and offer insights and automated remediation.
Runtime Application Self-Protection (RASP)
Runtime Application Self-Protection (RASP) is a security technology that provides an additional layer of protection for applications by detecting and preventing attacks in real-time. It is designed to monitor an application during runtime and prevent malicious activity that may not be detected by traditional security measures such as firewalls, intrusion detection systems (IDS), and antivirus software.
RASP works by embedding security controls directly into the application or the runtime environment. The security controls are designed to monitor the application’s behavior, detect any suspicious activity, and take appropriate action to prevent the attack. For example, RASP can prevent SQL injection attacks, buffer overflows, and cross-site scripting (XSS) attacks.
3 Types of Application Security Testing
Application security testing can be categorized into three types: black-box, gray-box, and white-box testing.
Black-Box Security Testing
In black-box security testing, the tester or test automation application does not have information about the internal workings of the system. This allows the tester to simulate a real attack by an external entity.
Black box testing has the important advantage that it tests application security from end to end, including security misconfigurations and the integration between security systems. For example, if there is a misconfiguration in the firewall, a black box test will immediately discover it because it attempts to access the application like an outside attacker. The disadvantage is that it can miss vulnerabilities in the underlying applications.
Gray-Box Security Testing
In gray-box security testing, the tester or automated test application has limited information about the application. This simulates the case of a privileged insider who uses their knowledge to conduct a more sophisticated attack or a persistent threat conducting in-depth reconnaissance of the environment.
Gray box testing has the advantage that it balances between testing depth and efficiency. It can be fine-tuned to focus on the most important elements that need to be tested in your security posture. Its disadvantage is that, depending on the information provided to the tester, the test may be skewed or unrealistic.
White-Box Security Testing
In white-box security testing, a human tester or automated testing mechanism receives full access to the internals of the application. A classic example of white box testing is static application security testing (SAST), in which an automated tool scans application source code for bugs and security flaws.
White-box testing can help uncover many important security issues, such as security misconfiguration in the application itself, poor code quality, insecure coding practices, and business logic vulnerabilities. Its primary advantage is that it is comprehensive and can identify issues that other types of tests miss. However, white-box testing can uncover issues that cannot be easily exploited by an outside attacker, and thus have lower priority.
Related content: Read our guide to mobile app security testing.
Application Security Testing Best Practices
Here are some best practices for effective AST:
- Start early: AST should be started as early as possible in the application development lifecycle, ideally during the design and planning phase. This allows security considerations to be built into the application from the start, rather than trying to retrofit security later on.
- Use multiple testing techniques: A combination of static and dynamic testing techniques can provide a more comprehensive view of the application’s security posture. This can help identify a wider range of vulnerabilities than using a single technique alone.
- Test regularly: AST should be performed regularly, especially during code changes or updates. This ensures that any new code is tested for vulnerabilities before it is deployed.
- Prioritize vulnerabilities: Not all vulnerabilities are created equal. Prioritize vulnerabilities based on their severity and potential impact, and address the most critical vulnerabilities first.
- Involve all stakeholders: Application security is everyone’s responsibility. Involve all stakeholders, including developers, testers, and operations teams, in the AST process to ensure that everyone is aware of the risks and taking appropriate actions.
- Monitor and respond to findings: The AST process is not a one-time event. Continuously monitor the application for new vulnerabilities and respond to findings promptly to ensure that the application remains secure.
Application Security Testing with Bright Security
For a robust AppSec programme, it is important to ensure that security vulnerabilities are detected and remediated early and often. With agile development and CICD, security testing needs to shift left and into the hands of developers.
To succeed, you need to adopt developer-friendly security testing tools like Bright’s DAST scanner, built from the ground up to enable developers to own the security testing process, with the following key features:
- Developer first – built for DevOps / CICD
- Test everything – WebApps and APIs (SOAP, REST, GraphQL)
- Accurate – NO false positives
- Automation – integrated automatic validation of findings removes manual validation bottlenecks that stifle your release cycles and compound your technical and security debt
- Feedback Loop – Easy to use, fast scans and integrates across your pipelines
- Easy fixes – Developer friendly remediation guidelines, start fixing security issues early and often
- Detect more – automatic Business Logic vulnerability detection
See Additional Guides on Key Cybersecurity Topics
Together with our content partners, we have authored in-depth guides on several other topics that can also be useful as you explore the world of cybersecurity.
UEBA
Authored by Exabeam
- What Is UEBA (User and Entity Behavior Analytics)?
- What Is UEBA and Why It Should Be an Essential Part of Your Incident
Response - UEBA Tools: Key Capabilities and 7 Tools You Should Know
What Are TTPs
Authored by Exabeam
- What Is Lateral Movement and How to Detect and Prevent It
- What Are TTPs and How Understanding Them Can Help Prevent the Next Incident
- 9 Lateral Movement Techniques and Defending Your Network
Disaster Recovery
Authored by Cloudian
- What Is Disaster Recovery? – Features and Best Practices
- The Easy Way to Create Your Own IT Disaster Recovery Plan
- What Is a Disaster Recovery Plan? 4 Examples



