The term penetration testing (pentesting) refers to processes, tools, and services designed and implemented for the purpose of simulating attacks and data breaches, and finding security vulnerabilities. You can run a pentest for a computer system, an entire network, or a web application.
The main goal of a pentest is to discover vulnerabilities that attackers can exploit. There are several ways to discover these vulnerabilities. You can opt for manual pentests performed by a team of white hat hackers, or automated penetration testing performed by a software solution.
The penetration testing process typically involves several phases. First, the tester (or solution) gathers information about the target and identifies possible entry points. Then, the tester attempts to breach the tested environment. Finally, the tester compiles a report detailing vulnerabilities found and suggestions for improving security of the tested environment.
This is part of an extensive series of guides about Cybersecurity.
In this article, you will learn:
- Why is Security Penetration Testing Important?
- Penetration Testing Process
- Penetration Testing Use Cases
- 6 Penetration Testing Types
- Penetration Testing Services
- Penetration Testing Tools
- Penetration Testing Best Practices
Why is Security Penetration Testing Important?
Penetration testing attempts to compromise an organization’s system to discover security weaknesses. If the system has enough protection, security teams should be alerted during the test. Otherwise, the system is considered exposed to risk. Thus, penetration testing can contribute to improving information security practices.
A “blind” penetration test, meaning that security and operations teams are not aware it is going on, is the best test of an organization’s defenses. However, even if the test is known to internal teams, it can act as a security drill that evaluates how tools, people, and security practices interact in a real life situation.
Penetration testing is usually unstructured and creative. For example, while one test could use a brute force attack, another test might attack company executives via spear phishing. This creativity is important, because sophisticated attackers will use the same skills and creativity to identify the organization’s security weaknesses.
Another benefit of penetration testers is that it is conducted by external contractors, and it is possible to determine how much information to divulge about internal systems. A penetration test can simulate an external attacker, with no knowledge of the internal network, or a privileged insider.
Learn more in our detailed guide to penetration testing tools.
Penetration Testing Process
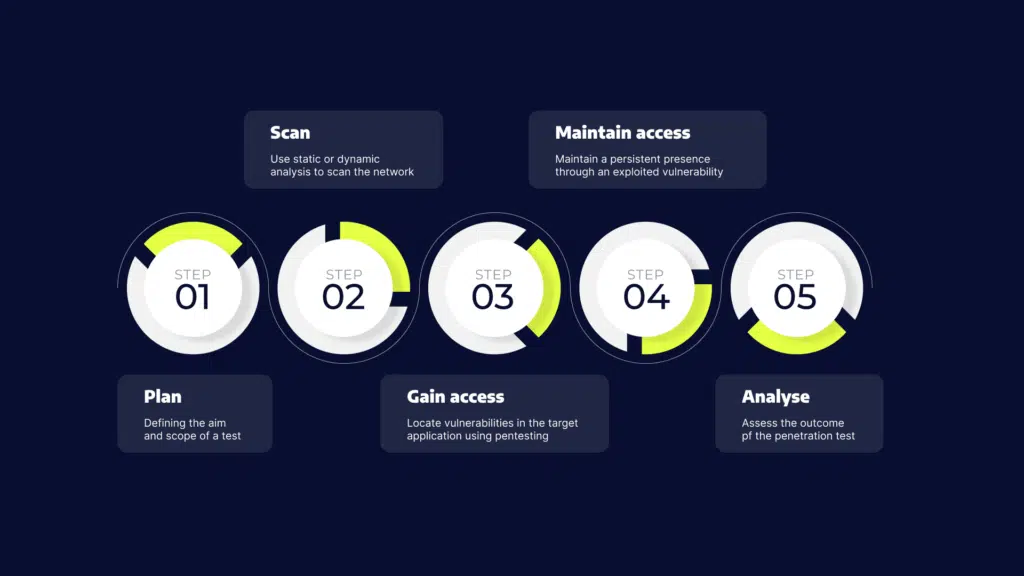
Penetration testing involves the following five stages:
- Plan – start by defining the aim and scope of a test. To better understand the target, you should collect intelligence about how it functions and any possible weaknesses.
- Scan – use static or dynamic analysis to scan the network. This informs pentesters how the application responds to various threats.
- Gain access – locate vulnerabilities in the target application using pentesting strategies such as cross-site scripting and SQL injection.
- Maintain access – check the ability of a cybercriminal to maintain a persistent presence through an exploited vulnerability or to gain deeper access.
- Analyse – assess the outcome of the penetration test with a report detailing the exploited vulnerabilities, the sensitive data accessed, and how long it took the system to respond to the pentester’s infiltration.
Penetration Testing Use Cases
Organizations use penetration testing for large and complex business-critical operations, as well as for custom components. Pentesting is necessary when developing software that handles sensitive data, such as financial assets, customer information and transaction data. Sensitive sectors—including government, medical and financial services industries—are highly regulated and thus require strong security measures.
If your organization has been infiltrated, you can leverage pentesting to help identify the weaknesses that enabled the breach and learn how to remediate them. You can also detect other vulnerabilities, which may not have been exploited, to prevent further attacks in the future.
Related content: Read our guide to penetration testing in aws.
6 Penetration Testing Types
Network Services Penetration Testing
The term network services testing, also known as infrastructure testing, refers to a type of pentest performed for the purpose of protecting the organization from common network attacks.
The goal of a network services pentest is to discover the most exposed security weaknesses and vulnerabilities in the network—before attackers can exploit these blindspots.
A network services pentest typically checks various components of the infrastructure, including servers and firewalls, switches and routers, workstations and printers.
Ideally, a network services test can help you protect against common network attacks, such as firewall misconfiguration, router attacks, switching or routing-based attacks, database attacks, man in the middle (MITM) attacks, proxy server attacks, and more.
Since mission-critical systems rely on the health of the network for continuous availability, organizations should perform external and internal network services pentesting on an annual basis, at least.
Related content: Read our guide to network penetration testing.
Web Application Penetration Testing
The purpose of a web application pentest is to identify security weaknesses or vulnerabilities in web applications and their components, including the source code, the database, and any relevant backend network.
A web application penetration testing process typically performs the following three phases:
- Reconnaissance—gathering information about the application. For example, the operating system (OS) and resources the application uses.
- Discovery—attempts are made to detect vulnerabilities.
- Exploitation—using the detected vulnerabilities to gain unauthorized access to the application and its pools of data.
The results of a web application pentest should provide information about detected vulnerabilities and any successful exploitation. This information can help the organization prioritize vulnerabilities and determine how to apply fixes.
Learn more in our detailed guide to web application testing.
Physical Penetration Testing
A physical pentest is performed for the purpose of discovering any vulnerabilities and issues in physical assets, such as locks, cameras, sensors, and barriers, that may lead to a breach.
For example, a physical pentest can assess whether attackers can gain unauthorized access to a server room. This access can serve as a point of entry into the corporate network.
Physical penetration testing can also assess how the organization copes with physical security threats like social engineering, badge cloning, tail-gating, and more.
By the end of this pentest, the organization is supplied with information about discovered physical security flaws and suggestions for mitigation.
Social Engineering Penetration Testing
A social engineering attack targets employees of the company or parties with access to company assets, trying to persuade, trick, or blackmail them into disclosing information and credentials.
A social engineering pentest tries to determine how the organization copes during a social engineering attack. In the end of this test, the organization is provided with information that can help create or improve a social engineering awareness program and related security protocols.
Client Side Penetration Testing
A client-side pentest is performed for the purpose of detecting software vulnerabilities that can be easily exploited on a client device like workstations and web browsers.
A client-side pentest can typically identify specific attacks. For example, cross-site scripting (XSS) attacks, form hijacking, HTML injections, clickjacking attacks, and malware infections.
Learn more in our detailed guide to penetration testing as a service.
Mobile Application Penetration Testing
A mobile application pentest attempts to discover vulnerabilities in mobile applications. This test does not include servers and mobile APIs.
Mobile application penetration testing usually involves the use of the two following test:
- Static analysis—involves extracting elements like source code and metadata, for the purpose of performing reverse engineering.
- Dynamic analysis—involves looking for vulnerabilities during runtime. The tester, for example, may try to extract data from the RAM or bypass controls.
Penetration Testing Services
There are two types of penetration testing services: manual and automatic.
Manual penetration testing is extensive and systematic. It is usually performed by a contractor or security consultancy, who agree on a specific testing scope with the client. Within that scope, an ethical hacker searches for vulnerabilities, attempts to breach the organization’s systems, and prepares a detailed report showing what they discovered and suggesting remediations.
Penetration testing as a service (PTaaS) is a new model, which provides an automated platform organizations can use to perform penetration testing on their systems. PTaaS systems use technologies like automated vulnerability scanning, dynamic application security testing (DAST) and fuzzing, to find security weaknesses and attempt to exploit them, without human intervention.
Learn more in our detailed guide to penetration testing types.
Manual Test Pros and Cons
Manual penetration testing pros
- Uncovers business logic vulnerabilities, as opposed to generic vulnerabilities which are easy to discover via automated tools
- Human penetration testers still use automated tools, so they are able to combine automated scans with manual exploration and analysis
- False positives are not a concern, because the penetration tester validates all findings before producing their report
- Ability to simulate complex attack campaigns involving multiple threat vectors
- Ability to identify zero-day vulnerabilities
Manual penetration testing cons
- Strongly depends on the skills of the tester. An unskilled tester, or one without relevant experience in the organization’s industry or technology stack, can miss important vulnerabilities and insights.
- Complex setup from the organization’s perspective, requiring contracts, detailed definition of scope, and coordination with internal stakeholders.
- High cost and large effort required to perform each penetration test
- Typically only possible to perform tests on a quarterly or annual basis, leaving the organization open to zero day threats or vulnerabilities resulting from changes to production systems
Learn more in our detailed guide to penetration testing report.
Penetration Testing as a Service (PTaaS) Pros and Cons
PTaaS pros
- Self service model, letting the client specify via a web interface on which systems, and at which frequency, to perform each test
- Makes penetration testing practical for companies with a smaller security team, or no security team
- Lower costs and flexible payment models – most services provide subscription or pay-per-use pricing
- PTaaS platforms can provide automated reporting that suits the needs of the organization, including specific compliance requirements
PTaaS cons
- Places more responsibility on the organization, as they need to determine the testing schedule and review findings independently
- Some cloud providers require permission to run automated penetration testing on their infrastructure, and limit testing to a specific time window
- If encryption is used for systems under test, this can complicate the use of PTaaS services
- Most services cannot identify business logic vulnerabilities
- More false positives compared to manual testing
Bright – a PTaaS service that automates many aspects of manual penetration testing
Bright provides PTaaS platform, which overcomes many of the disadvantages of manual PTaaS services. It uses artificial intelligence (AI), fuzzing techniques, and rich threat intelligence to detect a long list of known vulnerabilities in addition to zero-day attacks and business logic vulnerabilities.
In addition, Bright utilizes browser automation to provide zero false positives – it scans multiple layers of your environment including web applications and APIs and provides comprehensive reports, on par with reports provided by manual penetration testers.
Penetration Testing Tools
The types of pentesting tools you chose significantly impact the quality and results of the test. A tool might be able to catch a vulnerability, or it could miss it altogether. Typically, a pentest leverages several types of tools to ensure visibility into a greater scope of vulnerabilities and weaknesses. Here are several tools commonly used for pentesting:
| Pentesting Tools | Value | Pentesting Use Cases |
| Vulnerability Scanner | Scans the environment and attempts to detect known vulnerabilities and configuration errors. | Analyze the report generated by the scanner. The goal is to find an exploitable vulnerability to help penetrate the environment. |
| Web Proxy | An intermediary server that separates end users from the web pages they attempt to browse. | Intercept and modify traffic as it flows between the web server of the organization and the browser of the pentester. The goal is typically to detect and exploit HTML vulnerabilities and then use them to launch attacks. |
| Network Sniffer | Collects and analyzes network traffic. | Locate active applications. The goal is to hunt exposed credentials or sensitive data that is currently flowing across the network. |
| Port Scanner | Detects open ports. | Open ports provide information about applications and operating systems (OS) with network access. The goal is to identify potential attack vectors. |
| Password Cracker | A program that attempts to recover passwords that are either stored or transmitted in a scrambled form. | Find weak passwords that can provide access to the network. The goal is to leverage passwords to elevate or expand the level privileges and gain unauthorized access to the network and its assets. |
Penetration Testing Best Practices
Here are a few best practices you can use to improve the effectiveness of penetration testing activity.
Reconnaissance and Planning is Crucial
Penetration tests should start with vulnerability scans, and an open exploration for security gaps. Just like a real attacker, a penetration tester should perform reconnaissance against the target organization, gathering information from available resources, and planning the most effective exploits.
It is advisable to carefully record this stage, including vulnerabilities which were discovered and not exploited in the actual test. This can allow developers to reproduce and fix defects in the future.
Related content: Read our guide to penetration testing black box.
Build Attacker Personas
A penetration tester should think and act as an attacker. They should consider the cyber attackers motivation, goals, and skills. Motivation is an important factor in understanding hacker behavior. For example, a hacker looking to perform financial fraud will act differently from one seeking to exfiltrate sensitive data, or a hacktivist looking to do damage.
Before performing penetration tests, the organization should identify the personas of its most likely attackers, rank them, and focus tests on the most appropriate persona.
Freeze Development in Penetration Testing Environment
Successful penetration testing requires a known, stable state of the system under test. Adding a new patch or software package, changing a hardware component, or changing configuration, will invalidate the penetration test, because vulnerabilities discovered may not exist after the update.
It is not always possible to predict the positive or negative security consequences of an update—which is the reason to perform penetration testing in the first place. If there is no choice and systems must be modified during a test, this should be communicated to the attacker and taken into account in the penetration test report.
Learn more in our detailed guide to penetration testing and vulnerability assessment.
Automated Penetration Testing with Bright
Bright enables organizations to automate black-box testing for a long list of vulnerabilities across both applications and APIs. These tests include both technical vulnerabilities and business logic vulnerabilities. This combination goes a long way towards providing unparalleled coverage that previously could only be achieved by conducting manual penetration testing.
Moreover, the automated solution enables organizations to run targeted scans early in the SDLC and remediate issues before they make it to production. This is far superior to having to detect vulnerabilities in a production environment with manual tests.
Learn more about automated penetration testing with Bright
See Additional Guides on Key Cybersecurity Topics
Together with our content partners, we have authored in-depth guides on several other topics that can also be useful as you explore the world of cybersecurity.
Device42
Authored by Faddom
- Device42: 5 Key Features, Limitations, and Alternatives
- Device42 Pricing: The 5 Pricing Tiers Explained
- Device42 CMDB: Pros, Cons, and a Quick Tutorial
Disaster Recovery
Authored by Cloudian
- What Is Disaster Recovery? – Features and Best Practices
- What Is BCDR? Business Continuity and Disaster Recovery Guide
- Disaster Recovery Plan: 4 Examples & 10 Things You Must Include
Deserialization
Authored by Bright Security
- Deserialization: How it Works and Protecting Your Apps
- Deserialization in Java and How Attackers Exploit It
- Deserialization Vulnerability: Everything You Need to Know –



